Welcome to the Security in the News roundup for the week of 6/8/2025.
If you’re not familiar with the term “IoT,” it means Internet of Things, and encompasses devices including your cell phone as well as your Internet enabled-dryer or Internet-connected thermometer.
This opening article is a bummer, Wazuh is my favorite tool for SIEM (because it’s free!). It appears to be vulnerable, and worse, it’s the Mirai botnet rearing its ugly head. Here’s this story from Security Week:
Mirai Botnets Exploiting Wazuh Security Platform Vulnerability
Wazuh is a Security Information and Event Management (SIEM) system. This means it connects to various sources and analyzes those sources to determine if there’s a security event going on. The SIEM tools like Wazuh can comb through Snort alerts, for example. They can read your syslog to see if anything untoward is happening there. Then they can summarize and present the alerts on dashboards that are easier to understand than just looking at the raw logfiles.
In Wazuh, if I am recalling my setup correctly, there’s a server, and indexer, dashboards running on a server(s), and then there’s an agent running on each device you want monitored.
I’m going to steal this official sounding summary from Google’s AI Overview:
“Wazuh is a free and open-source security platform that provides threat detection and response, endpoint security, and compliance management capabilities across various environments, including on-premises, virtualized, containerized, and cloud-based deployments.”
Google AI Overview
The article goes on to say:
“An unsafe deserialization vulnerability allows for remote code execution on Wazuh servers,” the developers explained. “The vulnerability can be triggered by anybody with API access (compromised dashboard or Wazuh servers in the cluster) or, in certain configurations, even by a compromised agent.”
The thing to notice here is there was no period of what I’m calling “irresponsible non-disclosure.” The vulnerability was broadcast and the company quickly took care of the problem, with some reputational damage deserved.
More reputational damage was buried in the story a bit, from the article:
One Mirai botnet variant has targeted the flaw since early March, with the exploit designed to fetch and execute a malicious shell script that serves as a downloader for the Mirai malware payload. The same botnet also targeted vulnerabilities in Hadoop YARN, and TP-Link and ZTE routers. (emphasis mine)
Note the casual reference to “targeted vulnerabilities in TP-Link and ZTE routers.” You really just can’t trust any router, now, can you?
MIRAI BOTNET
The Mirai botnet phenomenon goes back to 2016. I never really understood it, so I did a little bit of a dive into the related Wikipedia page:
Mirai then identifies vulnerable IoT devices using a table of more than 60 common factory default usernames and passwords, and logs into them to infect them.[5][14][15] Infected devices will continue to function normally, except for occasional sluggishness,[14] and an increased use of bandwidth.
Note that any of us could be infected with this and not be aware. How often do any of us manually log into and check our security cameras? None, for the most part. We use our Wzye app or whatever apps you use, like HomeAssistant or a manufacturer’s app. They are all susceptible to Mirai, and they likely do not actively check for it. Windows Defender does claim to prevent Mirai, for what it’s worth. (see end of article in case the previous “claim” link doesn’t work).
It gets worse, Mirai remembers your device, if rebooted it comes back:
A device remains infected until it is rebooted, which may involve simply turning the device off and after a short wait turning it back on. After a reboot, unless the login password is changed immediately, the device will be reinfected within minutes.[14] Upon infection Mirai will identify any “competing” malware, remove it from memory, and block remote administration ports.[16]
It’s still around, for example from this January, 2025 story:
Mirai Botnet Launches Record 5.6 Tbps DDoS Attack with 13,000+ IoT Devices
This is one of many reasons why we should generally be against security cameras in our homes. Even if these cameras are not directly hacked through unknown backdoors or vulnerabilities in your router (and perhaps you still have a default password on your cameras?), these “cameras of convenience” are still a greater risk than most of us want to take. The risk of someone seeing into our houses on our security cameras should be taken seriously.
It might be fine to have cameras watching the outside of your home, but attacks on cameras are common, here’s a recent one. This article appears to be outside the paywall area on the Wired site:
A Brand-New Botnet Is Delivering Record-Size DDoS Attacks
From the article:
Eleven11bot is most likely a variant of Mirai, a family of malware for infecting webcams and other Internet of Things devices. Mirai debuted in 2016, when tens of thousands of IoT devices infected by it delivered what at the time were record-setting DDoSes of about 1 Tbps and took down security news site KrebsOnSecurity for almost a week. Shortly after that, Mirai developers published their source code in a move that made it easy for copycats everywhere to deliver the same massive attacks.
Let’s wrap up this week with this paper I stumbled across:
A Study of Common Vulnerabilities in IoT Devices
(paper once logged in)
In this paper on the surface we have a plain vanilla survey of IoT devices. The paper is not rocket science but it was an interesting read. They did two “experiments.” First they proved that a TP-Link Tapo C200 camera indeed was vulnerable to attack when the firmware wasn’t updated. Then they claim to have effected the same attack on a supposedly fixed “upgraded” version of the firmware.
Next they did some attacks against a CP-Plus E21A camera from “Aditya Infotech
Ltd. (CP Plus), … an Indian business that makes wireless IP cameras in addition to other goods.”
In the case of the second camera, maybe someone can help me here. I didn’t initially see why, once you have the username and password for the camera, why is it a problem to access the camera with the Tuya app? Maybe I’m not understanding what Tuya is all about, based on their website it just seems like a camera utility, among other things.
But then I dug in and learned about a controversy I was not aware of. Just like some elements of the government are gunning for Tiktok because of China privacy concerns, the Tuya app is also being targeted, and perhaps for a valid reason.
Tuya may be the China threat that beats Russia’s ransomware attacks
Our last article is from The Hill. We don’t usually get directly into politics here and we’re still not. If you read into the article, you’ll find this nugget:
Remember, China’s Data Security Law dictates that both private and state or partially state-owned or controlled corporations must cede control over user data to the Beijing government.
This is a good reminder that staying away from Chinese-owned entities for storing your personal data is probably a good idea. Granted most people are not going to be on the radar screen of the Chinese government, and have nothing to worry about. But in these matters it’s not the actual damage that matters, it’s the prevention of potential damage.
For a future article I’m going to look into how to move out data closer to home so that our IoT devices don’t send our sensitive personal images into the cloud.
See you next week! And be sure to check out our most recent “Research in Education” article on procrastination.
NOTE: The Mirai botnet attack took advantage of the Log4Shell vulnerability you may have learned about in CS 6035, Defender claims to prevent this attack:
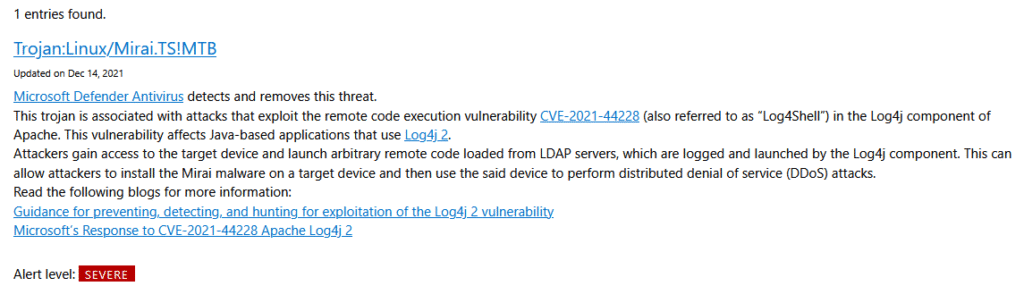
Image credit: “Coccinella Macro – Lady Bug – Dino Olivieri” by ! / dino olivieri / is licensed under CC BY 2.0.

