Welcome to the Security in the News article for the week of 6/16/25.
Just when you thought that ransomware hackers might keep their end of the deal when a hacking victim pays the ransom, think again:
Anubis ransomware adds wiper to destroy files beyond recovery
From Bleeping Computer, we have a story about Ransomware-as-a-service (Raas), Anubis. Not to be mixed up with the Android malware of the same name, in December 2024 the Anubis ransomware was first observed.
Now I suppose I never really thought this through, I knew that hacking tools are published and amateur hackers who don’t understand the tools can still use them. What I didn’t realize is there’s a fee-sharing agreement:
From the article:
A report from KELA at the time explained that Anubis offered ransomware affiliates an 80% share of their proceeds. Data extortion affiliates were offered a 60%, and initial access brokers a 50% cut.
Yes that’s right, there’s a ransom-sharing affiliate program for Anubis!
There’s another twist to Anubis. Even if they victim pays the ransom, Anubis has a file wiper feature. It will leave the file structure intact but set all files to zero bytes. Apparently the threat of wiping files is used to increase pressure on the victim to pay the ransom without delays.
Up next, when you click on Discord server invite vanity links, you have something to worry about:
Discord Invite Link Hijacking Delivers AsyncRAT and Skuld Stealer Targeting Crypto Wallets
If you are clicking a vanity link to a Discord server, be careful!
From the article:
The issue with Discord’s invite mechanism is that it allows attackers to hijack expired or deleted invite links and secretly redirect unsuspecting users to malicious servers under their control. This also means that a Discord invite link that was once trusted and shared on forums or social media platforms could unwittingly lead users to malicious sites.
Also from the article is this image:
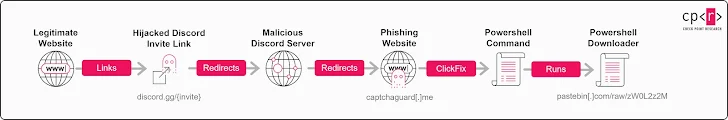
Honestly, reading the details, anyone with a pulse should be able to see through this.
Specifically, clicking the “Verify” button surreptitiously executes JavaScript that copies a PowerShell command to the machine’s clipboard, after which the users are urged to launch the Windows Run dialog, paste the already copied “verification string” (i.e., the PowerShell command), and press Enter to authenticate their accounts.
This is as bad as when a foreign call center scammer calls your grandmother and talks her into running something with the Windows Run dialog. Who aside from the technologically inept would actually follow all these steps to get access to a Discord server? Apparently some people are indeed getting fooled by this. You would think it would occur to these people to actually look at the command they are entering, but for a lot of people it’s probably just impossible to read/understand.
Which brings me to a point. Unless were talking about signed applications, just don’t run things on your computer without reading through them first. Granted, when I install Miniconda, I don’t read the entire install script, but I probably should, just to be sure nothing malicious is happening. Otherwise, you should not be executing commands on your computer that you don’t understand!